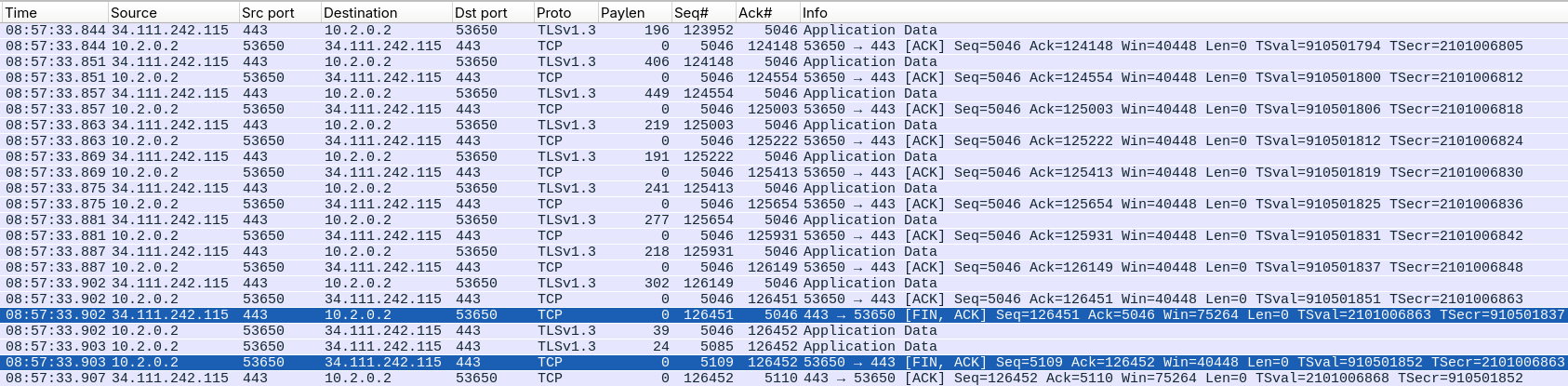
The problem seems to be as follows: every ProtonVPN server has a pool of addresses. Some or all of these addresses are marked by Google as high-risk, because a lot of simultaneous connections and/or attacks originate from them to Google properties. To prevent certain kind of attacks (Slowloris, resource depletion), Google tears down connections when the client is not sending data. Looking at a typical exchange with Wireshark, you will notice that if the model thinks more than 5 seconds, the connection will be torn down. If the model starts outputting its response before 5 seconds have elapsed, the connection will still be cut down exactly 5 seconds after the client sent its last TCP segment with a payload (i.e. the prompt). Although Wireshark shows my client sending many subsequent ACKs, none of these carry a payload, and they are thus not seen by Google as meaningful traffic:
A workaround would be to try another egress IP address by switching to a different ProtonVPN server. Anecdotally, this seems to work, which suggests that Google has not put the entire ProtonVPN IP range on its naughty list.
Seeing that Kagi is using Google infrastructure, they might also be able to do something about this by increasing this 5s teardown rule for high-risk IP addresses in their Google console. I do not know whether that is (1) possible or (2) desirable, though, as it might open them up to potential DoS.